Types of Data Security Risks
According to Think Teal, there are four foundational pillars for successful Hybrid Work Models. They are
- Highly Secure Environment
- Enhanced Employee Experience & Inclusivity
- Anytime, Anyplace Work Flexibility
- Improved & Sustainable Work Policies
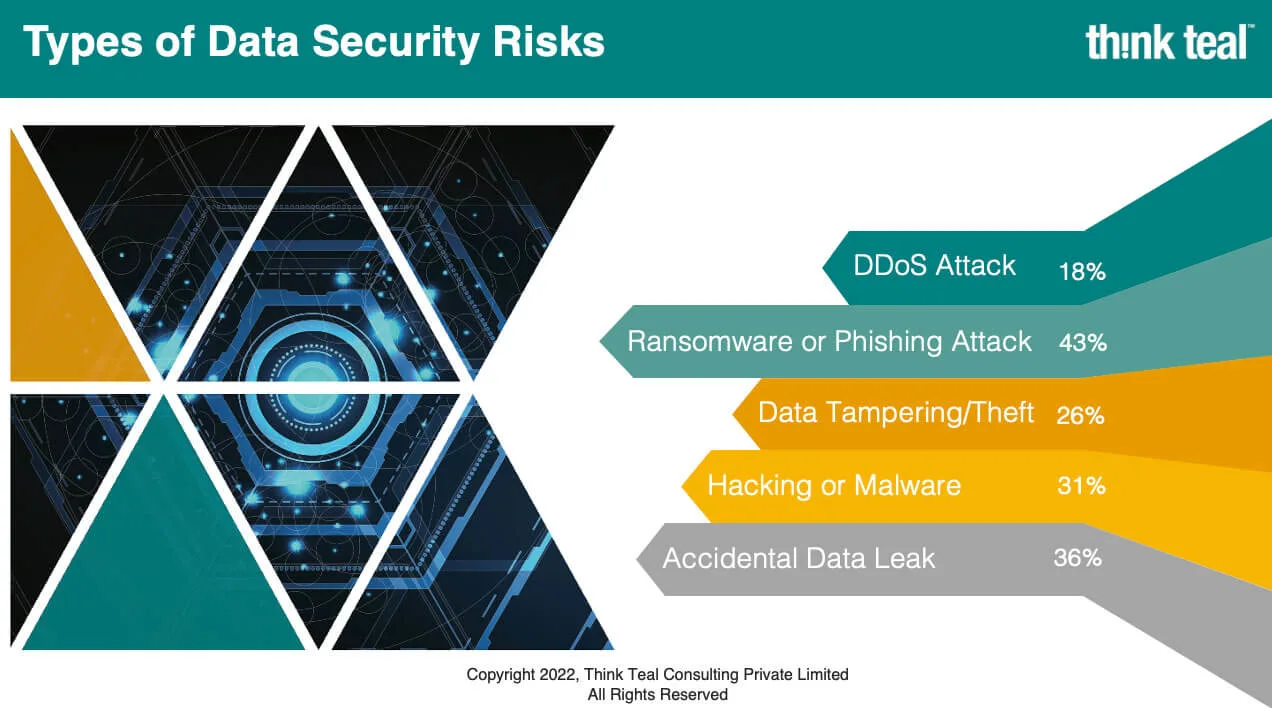
All four are equally important and require expertise to manage and maintain. Security is a horizontal without which no enterprise tech discussion is possible. The exhibit indicates that there are different threat vectors when we think about data security. They could be external or internal; they need not always be intentional. However, any lapse in data security has always had repercussions for business, not just financial losses but also brand reputation. And then there are compliance issues to deal with.
According to a recent research report by Ponemon Institute, the average cost of a data breach increased by 2.6% from $ 4.24 Mn in 2021 to $4.35 in 2022. It had risen by 12.7% in the 2020 report, a direct indication of the impact of hybrid work on data breaches.
While there are umpteen solutions available, choosing the right solution becomes a problem in itself!
Some of the trends that are prevalent in the cyber security market are:
- AI-powered Cyber Security – AI makes its position dominant in the security market. Like the financial services sector, where AI has helped in tackling frauds, similarly with AI, organizations can tackle security threats more intelligently by going through billions of data points to identify threat patterns.
- Securing “always on” IoT eco-system – As more organizations deploy IoT at scale, challenges around data protection are also emerging, like unencrypted data storage, botnets and malicious IoT devices.
- Privacy and Security – As we go ahead, we will see compliance and security being more interwoven than before. Issues related to privacy and GDPR compliance, among other things, will push many organizations to look at security from a different lens.
- Attacks beyond the perimeter – With hybrid work a de facto standard, greater use of cloud and interconnected supply chains have led to many new exposure areas, a combination of physical and digital security postures.